While deploying my application to Azure Web App, I would like to use the Cloudflare Access to protect my web application. So that only I can use the web application.
But the problem is the Azure Web App always assigns a custom domain to the web app (ex webapp-name.azurewebservices.net) so it could be scanned and accessed in public if anyone knows that domain. How we can prevent that?
1
It could be resolved if we can restrict access to the app from everywhere but Cloudflare Access.
There’re 4 steps we need to be done.
- Configure the Cloudflare Access to deny all.
- Add custom domain for Azure Web App.
- Enable the proxy mode for the DNS on cloudflare.
- Restrict all the traffic to the Azure Web App to be allowed from Cloudflare only.
1. Configure the Cloudflare Access to deny user
Go to Cloudflare Access and add an application with a policy to deny all users (except mine :D)

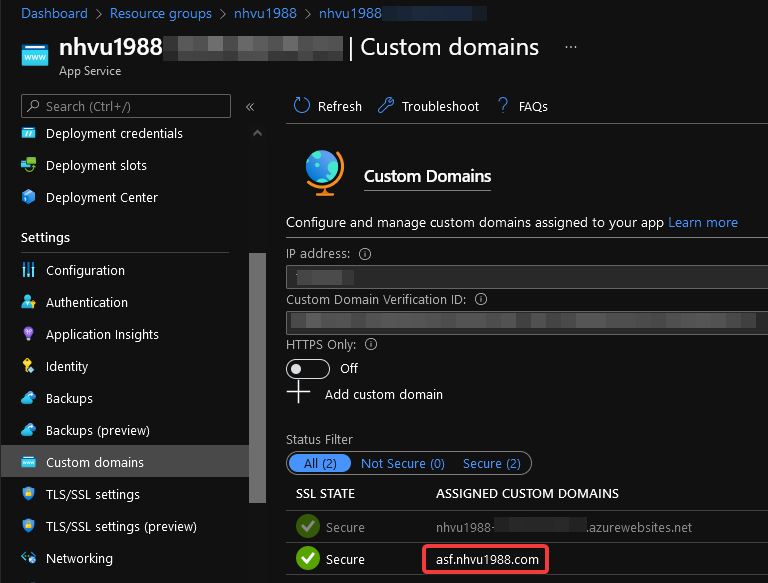
2. Add custom domain for Azure Web App
Ensure that the custom domain has been added and configured on Azure Web App…
3. Enable proxy mode for Cloudflare DNS
…and Cloudflare as well, but remember to enable proxy mode for it. So now all the traffic to Azure Web App will be proxied to Cloudflare.

4. Restrict all the traffic to the Azure Web App
Go to Networking - Access restriction
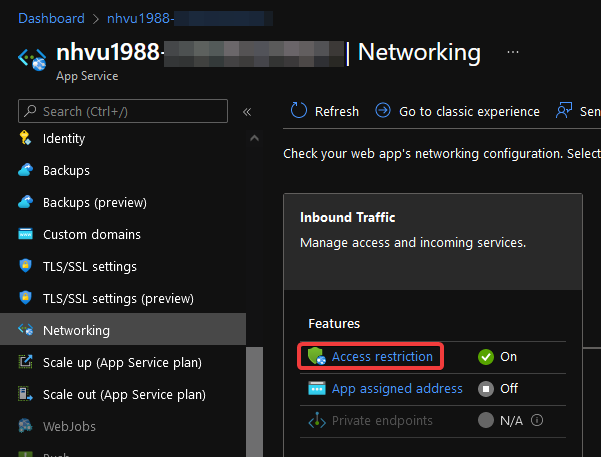
Add the Cloudflare Outbound IP Ranges to the rules.

But the issue is Azure Portal does not allow to add more than one IP range so you will see this error when adding it.

So you need to run the powershell scripts to add those IP Ranges directly on the Azure Portal Cloud Shell. Click on the Cloud Shell icon on the top-right of the portal, change the command prompt to PowerShell

And run the following commands
1
2
3
Add-AzWebAppAccessRestrictionRule -ResourceGroupName "resource-group-name" -WebAppName "web-app-name" -Name "Cloudflare Part 1" -IpAddress "173.245.48.0/20,103.21.244.0/22,103.22.200.0/22,103.31.4.0/22,141.101.64.0/18,108.162.192.0/18,190.93.240.0/20,188.114.96.0/20" -Priority 100 -Action Allow
Add-AzWebAppAccessRestrictionRule -ResourceGroupName "resource-group-name" -WebAppName "web-app-name" -Name "Cloudflare Part 2" -IpAddress "197.234.240.0/22,198.41.128.0/17,162.158.0.0/15,104.16.0.0/13,104.24.0.0/14,172.64.0.0/13,131.0.72.0/22" -Priority 100 -Action Allow
We need to slit them to 2 rules because of this error.
1
Add-AzWebAppAccessRestrictionRule: Cannot validate argument on parameter 'IpAddress'. Only 8 ip addresses are allowed per rule